One of companies’ top priorities is protecting their tangible and intangible assets from possible external threats. This makes it essential to have access management that acts as a protective shield and adds additional layers of security to traditional systems.
If you are thinking about implementing an access control system at your company or if you are already installing one, then this article is for you! We will tell you what access control is, what it is used for, which types are on the market, and how to pick the one that best fits your specific needs.
What is access control?
Access control consists of verifying the identity of users to authorize or deny their entry to restricted areas according to certain security parameters that the company itself establishes. These restricted areas can be both physical spaces—such as an office or parking lot—and internal areas of a building or company that require special protection—such as offices, cash rooms, server rooms, warehouses, etc.
In recent years, this type of solution has boomed and evolved enormously, reaching extremely high security levels.

What is access control used for?
The installation of an access control system for companies lets you manage, control and verify access to your different premises. It also makes it possible to automatically register entries and exits from a specific space, achieving complete tracking of all movements of both people and vehicles.
Thus, the main purpose of these systems is to administer and protect companies’ physical and intangible assets, through an online management system that will let you completely eliminate physical keys, leading to the reduction of operating costs and, in parallel, an increase in security.
In order for it to work properly, a good access control system should have a series of features:
- Easy to use.
- Flexible and scalable.
- Advanced management of users and doors.
- High-quality technical support that is readily available.
- Minimal maintenance due to ultra-durable top-quality materials and robust systems.
Further, all valued access control systems must be able to obtain real-time data, block unauthorized access and totally control and manage all accesses and visitors. Let’s analyze them in greater detail!
| For more information: Access control companies: What you should require of them |
Real-time data
An advanced access control system that ensures real-time management. The security manager must be able to consult permissions and accesses in real time. These permissions should update instantaneously.
Blocking of unauthorized accesses.
When implementing access control, it is essential to ensure that it immediately blocks any malicious or unauthorized access attempts. An advanced access control system should also send alerts when a registered user tries to get access outside of their assigned schedule or to enter an area for which they are not authorized. For example, it would be extremely useful for a company to know that a specific employee tried to access—finding the door locked—the door to the company’s warehouse in the early morning, when the company was not open, or if another user tried to access the cash management room, for which his credentials are not authorized. This point, added to the automatic logging of data that we will comment on below, lets you anticipate and prevent intrusion attacks very effectively.
Complete control and management of accesses and visitors
Entries and exits are automatically logged, which has a much greater impact than it may seem at first, as numerous studies claim that people tend to behave better when they are aware that they are being identified..
 |
Si te interesa conocer más a fondo cómo puede ayudarte NÜO Planet a solucionar los problemas de seguridad de tu instalación, te invitamos a descargar el caso de éxito de Step Up. |
Access control: the most common types
Access control systems can be classified by several different variables. Two of the most prominent are: the arrangement of the system and its components, and the identification method. The security level of the implementation is dependent on these factors.
Based on the layout of the system, access control systems are divided into three categories:
- Autonomous: they are not connected to any central system, so they are generally only used to permit access and cannot log accesses or block access.
- Centralized: there is a single coordinated system responsible for managing entries and exits, at multiple entry points.
In turn, depending on the identification method, there are four basic control types. Let's review them quickly.
Access control by keyboard
Entry to the premises is done by entering a code on the device’s keyboard. This method is quite unsafe, as the credentials can easily be intercepted by unauthorized persons, users can forget their code, and the keyboard mechanism can break over time.
Biometric access control
In this case, users’ physical and biological characteristics are employed to identify them and authorize access. This method is effective and increasingly more widespread, as technological advances have led to its democratization.
There are three main biometric identification methods:
- Fingerprint: this is the most secure of all access control types, since fingerprints are unique, inimitable, and impossible to clone and transfer. The most sophisticated systems include multispectral optical recognition, which provide great precision regarding speed and certainty in identification.
- Facial recognition: based on 2D and 3D images to extract a template and identify an individual. It is less secure than fingerprint identification because it is easier to manipulate and, in parallel, this technology is still not highly mature.
- Iris recognition: eye identification is more precise than facial, although it still has several problems that mean that it is still not widespread among companies. Its main disadvantages are that an individual’s height when facing the device must be exact for it to work correctly, and some users consider it an excessively intrusive method. The high price is another factor, as it provides a security level similar to fingerprint identification.
Access control with card
This access system employs an ID card that is read by a specific terminal. The safety of this method depends on the type of card chosen. Thus, low-frequency (125 kHz) proximity cards are vulnerable, while high-security cards, such as MIFARE Plus® are more secure.
Mobile access control
Users’ cell phones become the identification method to authenticate and authorize access by placing it in front of a reader. This method is extremely secure, since there is dual protection: the encryption of radio-frequency systems, added to the security system of the cell phone.
What is the perfect access control system for my company?
Attending to each company’s specific needs, the most suitable access control systems for proper protection will depend on the unique features of each installation. This makes it extremely important to hire a company with an expert security team that will provide you with personalized advice based on the needs of your project. Therefore, there is not a single best solution, but rather the one that best fits each concrete use case.
01. For SMEs, retail or homes
Simplicity is the key factor for SMEs, retail and homes. In this regard, having a system where everything is centralized in a simple and intuitive application, with extensive user experience, and no type of complexity is essential. At NÜO we make it really easy for you with NÜO Go!, the access control system for SMEs and homes that is totally adapted to your exact needs. For example, with a single touch of the entry reader you can in the simplest way possible just by putting your finger on the reader open the security shutters of your business, open the door, and deactivate the alarm, so that your store is open for business within seconds. This will give you not only great security, but it is also so convenient and easy.
In these cases, we also recommend securing the outside entrances to control pedestrian access, as well as vehicle access. You can do this by configuring the parking lot with a long-range UHF card reader, a video intercom to manage visitors, high-security card readers or cell phone opening, whichever your preference may be.
Another interesting function is the possibility of programming the doors that should open in the event of an emergency or evacuation, as well as those that should remain closed. Thus, your only concern will be to get out as quickly as possible.
You may also have the need to safeguard specific inside areas against visitors or unauthorized employees, such as:
For SMEs:
 |
 |
 |
 |
| Confidential document and archive rooms | Offices | Warehouses with valuable objects | Prototyping and R&D rooms |
 |
See all the possibilities for access control at SMEs here: Security for SMEs and offices |
For homes:
 |
 |
 |
 |
| Wine cellars | Changing rooms | Display cases with valuable objects | Private rooms to which you do not want visitors to have access |
 |
See all the possibilities for access control to homes here: Home security |
For retail:
 |
 |
 |
 |
 |
| Cash management rooms |
Product warehouses | Doors with airlock function for safeguarding high-value objects | Special functions such as supervisor mode. | Display cases with valuable objects. |
 |
See all the possibilities for access control to stores here: Security for the retail sector |
02. For corporate buildings or large companies:
What is most essential for corporate buildings and large companies is guaranteeing comprehensive tracking and control of the movements of all users, namely employees, visitors, occasional personnel and vehicles..
For employees, the best solution is to implement an access control system by shifts and smart elevators that authorize access by fingerprint, card or cell phone, thus increasing the security of your facilities. Vehicle access control is also necessary to efficiently manage the company’s parking lot..

And for visitors and service providers, a video intercom system is perfect so that you can clearly see the person, as well as having quality audio to make conversing easier. You should also have a reception area equipped with an application to efficiently manage visitors to the building. Thus, you can easily assign a security profile, limiting access by areas and times and you will have mobile credentials that you can send directly to visitors to prevent wasting time and improve the image of your organization, as well as devices to register fingerprints and print visitor badges that are activated in real time.
Another interesting option is being able to control the occupancy of your building and prevent a single ID from being used by several users.
 |
See all the possibilities to manage building security here: Access control for offices and buildings |
03. For industrial or logistics companies:
In the same way as for corporate buildings, you will also need to completely control users’ movements at factories and logistics companies, with an access system via turnstile and powerful video intercom systems.
We also recommend adopting other additional measures in this case. The first will be a visitor and employee access management system specially designed for intensive use under extreme weather conditions, resistant to typical factory settings that may be dusty and dirty, where users’ fingerprints may be eroded by chemicals or caked with oil or dirt, an environment in which the NÜO Awa fingerprint reader is number one.
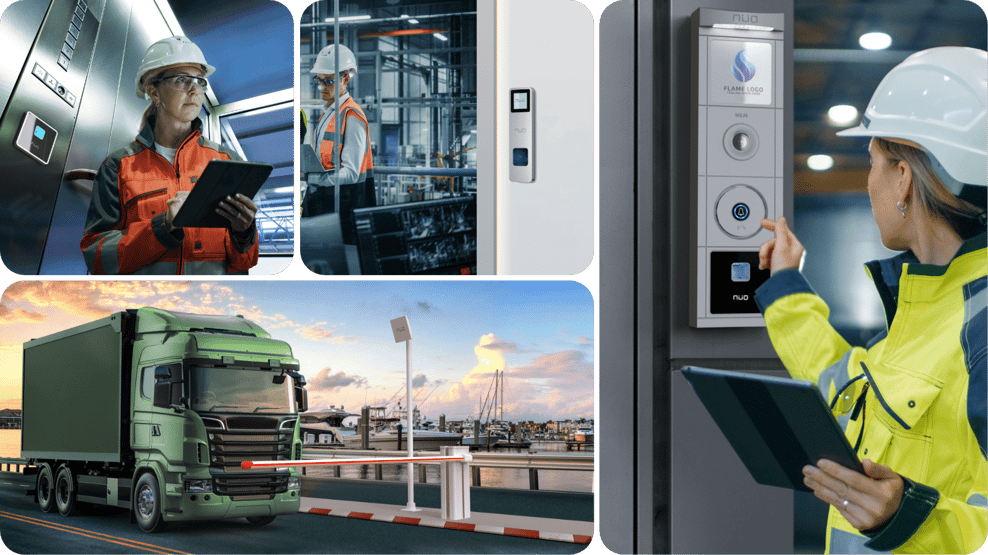
You will also need parking management solutions for the efficient organization of fleets and trucks, as well as access control for electric gates.
Of course, we cannot forget about sensitive areas such as hazardous substance warehouses or server rooms. Access to these facilities must be particularly restricted to users with permissions.
 |
See all the possibilities for access control in industrial environments here: |
For hospitals, clinics, and schools:
LHospitals, schools and universities are characterized by large flows of users going in and out that you must be able to monitor and control. That is the reason why the solutions to implement in this area have the added unique need of requiring 24/7 protection.

In this regard, entry control systems, occupancy control, and emergency evacuation systems become extremely important.
As an additional factor, it could be interesting to have assistance points placed throughout the campus or hospital grounds so that students or patients who need help can contact the secretary if they need information or have an emergency.

 |
See all the possibilities for access control to hospitals and clinics here: Security for hospitals and laboratories |
 |
See all the possibilities for access control to schools and universities here: Security for universities |
In short, access control is essential for ensuring data protection at companies, as well as the integrity of their structure and assets. It is ideal to implement sophisticated systems that guarantee security, as well as convenience and ease, and that they are easy to install. If you have any questions about which system would be best for you, please send us your query and one of our experts will contact you to guide you through the process to analyze and select devices.
Escrito por: NÜO Planet
Categorías: Access Control










